Secure by Design Done Simply
Discover and Mitigate Security Threats early during software design using the Tutamantic threat model services
Trusted by These Brands





3.5x Performance
Performance improvement for doing People (Online Training) + Process (Workflow Consulting) + Technology (Cloud Service)
Cisco Security Outcomes Study Vol 2
6.5x
Reduction
Cost reduction in security issues if remediated during planning
- IBM System Science Institute Relative Cost of Fixing Defects
16.97% Improvement
Average Improvement in overall business enablement if Online Training, Workflow Consulting and Cloud Services are done
Cisco Security Outcomes Study Vol 2
Discover Tutamantic's innovative threat modeling services

Cloud Service
Re-use your own diagrams to create rich threat models using the Tutamen threat model automation cloud service

Online Training
Learn how to do threat modeling from one of the world's experts; Learn useful frameworks, Agile integration and the open-source Rapid Threat Model Prototyping methodology

Workflow consulting
Our highly-experienced consultants will identify optimal integration points for threat modeling in your development and build processes.


Automated Threat Model Security with Our Cloud Services
Add another security layer to your software design
Tutamantic's proven automated cloud service can turn your diagrams (e.g. drawio, Terraform, Visio, Lucidcharts) or infrastructure schemas into living threat models.
Add metadata describing the security to your design and the cloud service will automatically generate threats, mitigations, threat paths and areas of maximum concern.
Top-quality Online Training in Threat Modeling
Engineers who learn the Rapid Threat Model Prototyping (RTMP) methodology will experience between a 50 - 60% boost in being more effective in their roles. The course is based on real-world scenarios and attendees will be able to quickly grasp RTMP threat modeling as a result.
RTMP removes nonessential threat modeling steps and ties the most commonly used security frameworks directly to STRIDE, to enable a quick assessment of optimal security mitigations.
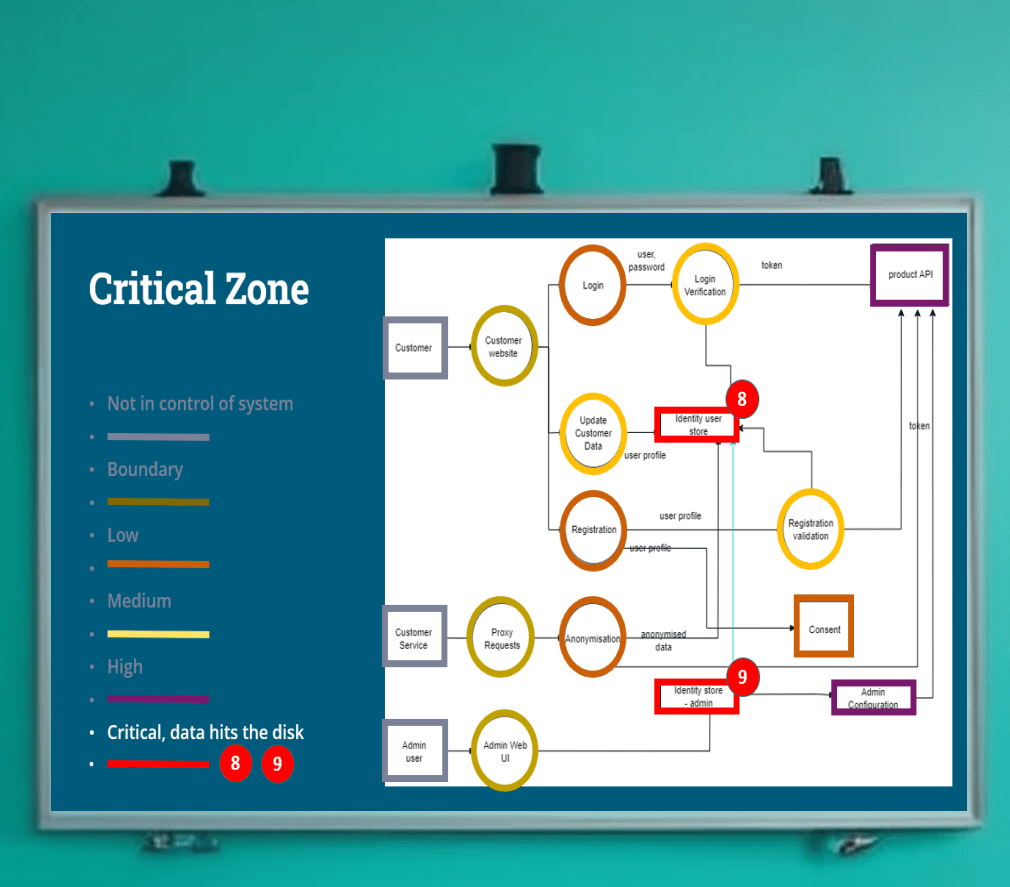

Proper Integration guidance for your build pipeline
Expert help to maximize your threat modeling outputs
Tutamantic's consultants will analyze the optimal integration points in your current build process and CI/CD automation chain.
They will then give guidance (schemas, code and default settings) for best threat modeling points and best use of threat and mitigation outputs in the processes.
Tutamantic Feedback
Our Testimonials of Experiences
[One of the] Threat Modeling Leaders You Must Follow in 2024!

Practical DevSecOps
company
Tutamantic provided a very good course. Packed a lot in to two days, but it has left me with a very good overview in what is required for producing threat models with a good degree of confidence.
Great trainer and course notes.

A. Young
Principal Systems Engineer
Great depth of experience in this space, combined with a no nonsense practical attitude to getting the job done, [...] training security champions, rapidly and measurably improving our maturity against the OpenSAMM framework [...] comes highly recommended ... .

Russ W.
Head of Information Security
Insights and Updates from Our Blog
Dive into our blog, understand security dynamics, keep abreast with Threat Modeling trends.
Let's Get In Touch
Connect with our dedicated team today
call our UK number
Monday - Friday
9 AM to 6 PM GMT
EMAIL ADDRESS
call our US number
Wednesday - Friday
8 AM to 3 PM EST
GET IN TOUCH
+44 0785943 932
+1 509 663 8923
Don't miss our new offerings and updates
© Copyright 2024, All Rights Reserved.
Privacy Policy
Terms & Conditions



